Multi-environment Reality and the New Security Challenges
We are now in the post-pandemic phase but still the hybrid work is continuing. There are many of us are settling with the permanent work-from-home option. COVID pushed IT to be distributed, and borderless and raised many challenges. And if you take a look at it from a technology transformation perspective the below figure narrates how, or why it makes it so difficult for organizations to be security resilient. It is the multi-environment reality that organizations are facing today.
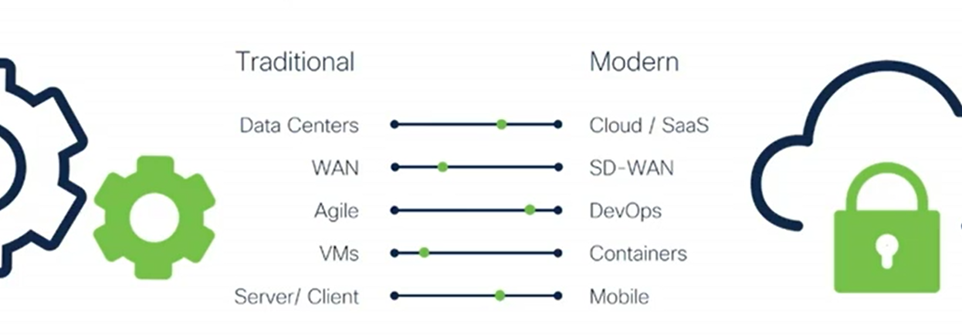
From the data center perspective, many companies have their application hosted both on-prem and also in the public cloud. Due to this fact, the attack surface is growing, and organizations need to come up with security probes that work in both environments.
And for the wide area network, we see the transition for this towards the software-defined wide area network, which adds a silver layer on top, that gives the flexibility to use any underlying transport methods that the organization wants such as internet, MPLS, Leased line, etc. However, this flexibility ease adjusted traffic patterns and resulted in additional security concerns such as branch direct access to the cloud and internet.
And also with this new DevOps style, security needs to keep up with the pace of application development. And these newly developed applications, also land on a different platform where traditionally they use virtual machines and they now land in containers. With this new microservices platform containers also needs a new way of looking at security.
Finally, the way how we consume these apps. Traditionally it was server client environments and currently, mobile APIs that need to be accessed. This raises questions about who’s accessing and who gets access to these APIs. and how to secure reachability, and so on. And think also about machine-to-machine connectivity and the related challenges
With this, some of the key questions around new security challenges are
- Do our customers actually have visibility on what’s going on?
- And how are they exposed?
- And even if customers are breached, how fast they can recover?
- And are we able to measure the progress made with regard to security?
- What does the reporting look like? And so on!
It’s not that these questions didn’t pop up before. But with the focus on resilience, we see that these questions are really top of mind and able to build that successful security resilience. It requires a shift from point-in solutions towards a more integrated and open approach. Traditional approaches were very threat centric. And today, we see that we focus more on detection and response, and recovery to build the required security-resilient environment.