VMware NSX Security Solution Analysis
Historically VMware is into virtualization. With the acquisition of Last-line VMware firmly started attacking the $5B security market. With the ongoing trend of distributed applications and with the growing east-west traffic the traditional approach of physical firewall appliances becomes very inefficient. For example, network changes have to occur to get the traffic funneled in and out of multiple physical appliances. Moreover trying to send all the traffic in a data center to the perimeter leads to performance and scale issues, and visibility becomes a huge challenge
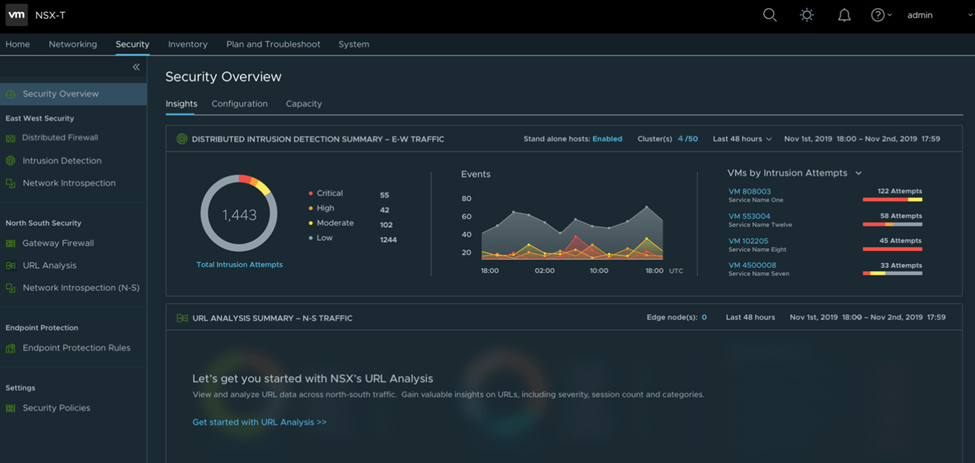
VMware NSX Security Solution Offerings
| Distributed Firewall: Complete L2-L7 capabilities | Distributed IDS/IPS | ATP | NSX Intelligence |
| Stateful Layer-4 Access Controls – Ability to write group-based policies between source and destination | Distributed & Built-in Analysis | NTA (Network Traffic Analysis) – Monitor east-west traffic and traffic flow records and flag traffic outside the norm as anomalies | Topology and Flow Visualizations – build topology maps, see them at the Data Center level, zoom into the Application level |
| Layer-7 Controls with AppID – ID-based policies, so you write them not based on port protocol, but on application traffic; can write a policy based on actual traffic you want to allow or deny as opposed to just the port protocol | Curated Signature Distribution – Fewer false positives, the lower computational overhead | Network Sandbox – used for emulating the operating environment, enabling organizations to probe suspicious files and other objectssnip | Automated Policy Recommendation – Discover the whole application, group similar services into a single application |
| Identity Firewall with UserID – for VDI micro-segmentation, when multiple users on a server with VDI desktop, you can create access policies based on user ID and not server ID | Context-Based Threat Detection – Reduce the need for signature tuning, better alert prioritization | NDR( Network Detection and Response) | |
| Policy & State Mobility – Simplify operations, eliminate stale/redundant policies |
Some Technical Considerations
Following are some of the key considerations
DFW and Edge VM:
- The same traffic can have distributed firewall, l7 app-id rules, and IDS/IPS rules
- Traffic needs to be allowed by DFW to be passed through to IDS/IPS
- No network overlay requirement if the customer wants to just use the security solutions
- NSX Gateway Firewall can now decrypt SSL traffic
IDS and IPS:
- The IDS/IPS engine is based on Suricata, a well-respected open-source project.
- IDS/IPS signatures come from Trustwave, a leader in managed security services
- The signature can be downloaded online to the NSX or can be uploaded offline
ATP (NTA, NDR, and Sandboxing):
- Sandboxing is based on Last-line solutions
Key Use Cases and Considerations
| Regulatory Compliance | Virtual Zones | Discrete Appliance Consolidation | Virtual patching |
| Enable software IDS/IPS for critical apps | Create zones in software without the cost/ complexity of air-gapped networks or physical separation | Replace discrete centralized appliances | Prevent lateral movement of attackers by blocking vulnerabilities |
| Easily achieve compliance requirements for PCI DSS, HIPAA, and SOX | Secure vendor-partner, provider-tenant traffic | Leverage native IDS/IPS implementation in NSX- simply turn it on | Combine signature-based detection, anomaly detection, and protocol conformance check |
| Eliminates blind spots |
Licensing types
Following are the stand-alone licenses specific to NSX-T security and there are add-on licenses available with the existing NSX bundle as well
- NSX Firewall
- NSX Firewall with Advanced Threat Prevention
- NSX Firewall with Bare Metal
Scale limits (NSX v4.0.1.1)
| Firewall | Distributed Firewall | Requirements |
| Logical Ports with Groups Applied | 25000 | |
| System-Wide Stateful Firewall Rules | 100000 | |
| Rules per Firewall Section | 1000 | |
| Rules per Group | 512 | |
| Firewall Section | 10000 | A Firewall Section equates to an OpenStack Security Group |
| Rules per Hypervisor Host | 120000 | Total rules across virtual NICs on a Hypervisor Host. |
| Rules per Virtual NIC | 4000 | |
| Saved Firewall Rule Configurations | 100 | Only for automatically created drafts configurations |
| Services | 8000 | |
| Objects per Firewall Rule | 128 | Total configuration objects or groups that can be used per rule inclusive of Source, Destination, Services, Context Profile and Apply To fields. |
| Firewall | Intrusion Detection | Requirements |
| Hypervisor Hosts | 512 | |
| IDS profile | 25 | Excluding the default |
| IDS Rules | 1000 | |
| Events recorded | 2000000 | Up to 14 Days |
| Firewall | Malware Protection | Requirements |
| Files Analyzed using Dynamic Analysis/Sandboxing per Day on Gateway Firewall | 15000 | Requires an Extra Large Edge Node |
| Files Analyzed using Static Analysis per Day on Gateway Firewall | 100,000 | Requires an Extra Large Edge Node |
| Malware Profles on Gateway Firewall | 50 | Requires an Extra Large Edge Node |
| Malware Detection Rules on Gateway Firewall | 500 | Requires an Extra Large Edge Node |
| Requires an Extra Large Edge Node | 100,000 | Up to 14 days of events stored. |
| Files Analyzed using Dynamic Analysis/Sandboxing per Day on Distributed Firewall | 30000 | |
| Files Analyzed using Static Analysis per Day on Distributed Firewall | 10000 | |
| Hypervisor Hosts | 512 | |
| Malware Profles on Distributed Firewall | 50 | |
| Malware Detection Rules on Distributed Firewall | 1000 | |
| File Events on Distributed Firewall | 700,000 | Up to 14 days of events stored. |
Competition
The competition for this solution is catered to two different target groups
| Firewall Vendors | Microsgementation Vendors |
| Checkpoint | Illumio |
| Cisco | Cisco Tetration |
| Fortinet | Guardicore |
Summary
NSX security solution covers several use cases for east-west traffic protection inside your server farm environment and claims to have more than 13K+ customers running this solution. the solution is the best fit if you have more than 95% of your workloads virtualized. For more information please visit the previous blogs on NSX-T

Thanks.