VMware NSX-T and Cisco ACI and Its Complimenting Use Cases
Running VMware NSX-T and Cisco ACI together on your Datacenter infrastructure is a debatable topic. And in many cases questioned by customers and partners. From the SDN perspective, both solutions claim to satisfy the customer requirement in some or other ways. However in this blog post of “VMware NSX-T and Cisco ACI and its complimenting Use Cases” let’s understand the best of both solutions. Which may help in planning and designing of your infrastructure.
Quick Analysis of VMware NSX-T
NSX-T is solely a software-based SDN solution that can run on x86 server platform. It offers many of the L4-L7 services, such as distributed firewall, routing, switching, IDS and load-balancer, VPN, NAT, DHCP, DNS relay, etc. VMware NSX-T uses GENEVE as the overlay and any physical hardware from any vendors for underlay connectivity
Quick Analysis of Cisco ACI
ACI provides the hardware and software required for running the SDN solution. And, positioned itself as an SDN fabric where you can attach all your physical and virtual L4-L7 services, Compute, and management solutions. It is apparent that the main focus of the solution is to enable centralized routing and switching and stateless firewalling across the fabric. It uses VxLAN as an overlay and IS-IS and MP-BGP for the underlay routing
Quick Analysis of the Datacenter Infrastructure
When it comes to providing seamless application services to its customers, the data center is a core infrastructure on which the whole business relies on. This is true; irrespective of you are into banking, insurance firms or real estate providers, oil and gas, or the healthcare sector, etc.
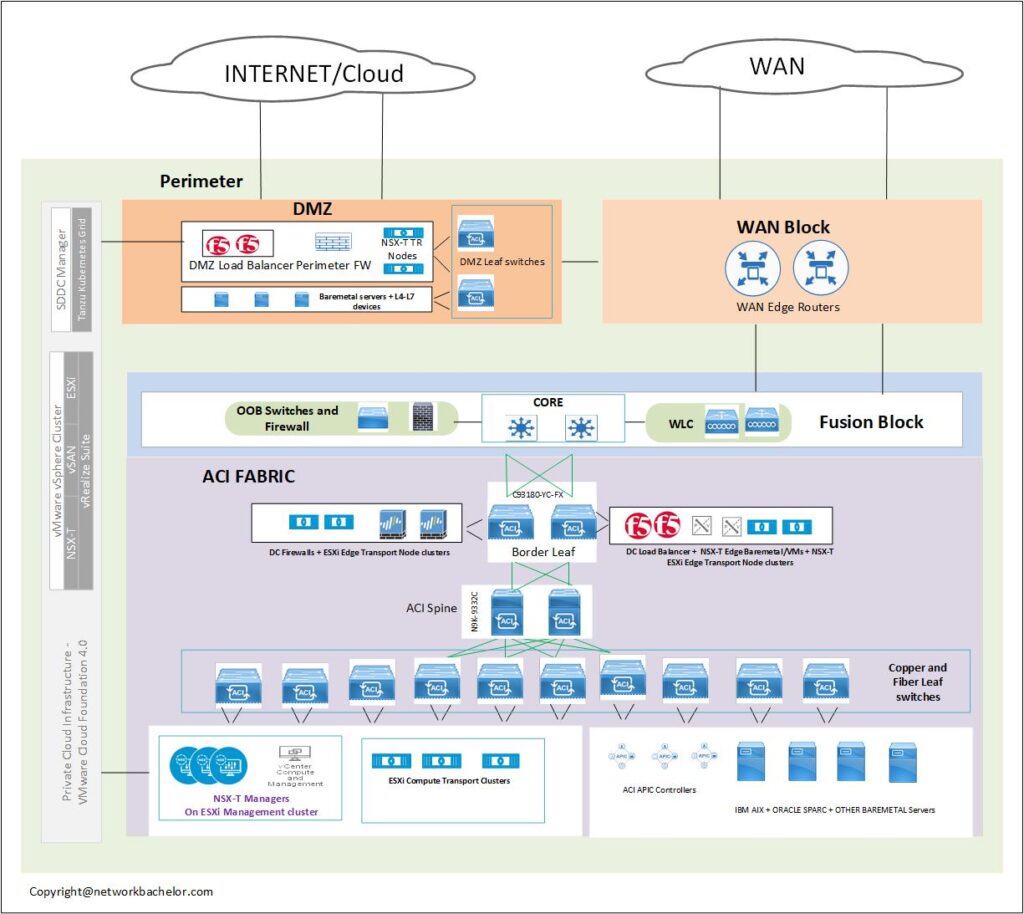
And the applications enabling the business are usually from different solution providers. It could be from vendors such as IBM, Oracle, Microsoft, SAP, Mobi-web, etc. Or from other ERP and CRM providers. Interestingly these application comes with own requirement in terms of required hardware and compatibilities. Hosting of some of these applications can be done on the hypervisors such as ESXi or Hyper-V. And others require its platforms like IBM AIX or Oracle SPARC servers.
If you look at the market data, the majority of organizations are already 70 to 95% virtualized. And most of the organizations left with few critical legacy applications on bare-metal servers. Result in the application traffic flow between these heterogeneous systems a challenge. Especially, when you have a mix of bare-metal and virtual servers or physical servers that do not support virtualization.
Now let’s get into some of the non-overlapping scenarios of co-existing VMware NSX and ACI
Use case of running VMware NSX
- Reduce the passive infrastructure blueprint:- Running distributed firewall, routing, switching IPS/IDS and VPN, etc on x86 platform reduces the need for having dedicated physical devices, intern reduces the power and cooling requirement in the infrastructure
- Private cloud automation across DMZ and DC:- with solutions such as VCF and vRealize automation and orchestration tools, It is possible to do the end-to-end automation of VM instance, virtual network, and storage. This intern result in quick provisioning of the application
- Granular micro-segmentation of workloads across DMZ and DC workloads:- The NSX-T distributed firewalling is a stateful firewalling which could span across the VMware infrastructure. It also supports features such as Context-aware and layer-7 capabilities. It will be a real and easy way for implementing micro-segmentation across your DMZ and DC workloads
- Single management to automate L4-L7 infrastructure and provisioning across the DMZ and DC:- The end to end security and networking capabilities such as load-balancing, service-chaining with third-party firewalling, and load-balancer ( Eg: Palo-Alto firewall, F5 load-balancers ). And native VPN and NAT capabilities are giving the best option for quickly setting up infrastructure for the applications.
- Seamless & faster infrastructure provisioning:- NSX-T brings all the agility and flexibility you need when provisioning end-end networking and security for hosting the application
- Visibility and Troubleshooting:– The network topology map and application flow visibility use case together it brings with the VRNI and NSX-T intelligence is one of the best in the industry. And the troubleshooting option on NSX-T using features such as trace-flow are some of the key tools to look for
Use case of running Cisco ACI
- Centralized Management of bare-metal and hypervisor server’s connectivity:- As shown in the topology, whether the environment has hypervisor or bare-metal based servers (Endpoints), all of these can be connected to the fabric. It effectively allows the centralization of the routing and switching function from the Cisco APIC controller. This intern results in centralized visibility and troubleshooting capability across the infrastructure
- Centralized connectivity management of physical firewall, load-balancer, and proxy, etc:- Cisco ACI key capability lies with physical fabric management. in-effect it provides physical switches to connect the servers and the other L4-L7 devices such as Cisco FTD, Fortigate, Palo-alto firewall or Citrix Netscaler, etc.
- Traffic switching between the physical and virtual infrastructure:- There will be many instances where the applications hosted on the vSphere environment need to talk to the application hosted on the bare-metal servers. Such as Oracle or IBM servers. Cisco ACI fabric could be a stable platform choice to do routing, switching, and security for these physically connected heterogeneous systems.
- Centralize traffic analysis and security rule creation ( stateless):- Fabric level segmentation of the traffic using EPG ( Endpoint group ) and micro-segmentation of the connected end-point are some of the use cases
- Programmable Physical Fabric:- The connected end-points properties such as physical link speed, link-aggregation, and VLAN trunking, etc can be centrally scripted using REST API.
- Logical segregation of physical and virtual connectivity – Multi-tenancy:– Use ACI tenancy construct (overlay-based) to do segregation of DMZ, Production, and UAT or DEV environment
- Zero-touch provisioning and maintenance of physical switches
Summary
The co-existence of VMware NSX and Cisco ACI could leverage the goodness of both solutions in your infrastructure. For sure, it has to be carefully planned based on the scenarios and use cases. And “yes”, there will be traffic flow of GENEVE tunnel running over the Cisco ACI VXLAN tunnel (Double tunneling) on the fabric. However, this should not be an issue as these traffics are generally east-west. Moreover, the east-west traffic is done through high capacity leafs switches multiple uplinks usually 40/100G links.
For more related blogs on the topic – please refer the section “Datacenter networking & security“ happy learning

Thank you for the post, got clarification on many of questions using this blog
Thank you Sari, glad to know it was helpful
Nice and crispy write-up. Appreciate the efforts!!!
Thank you Ashish