Zero-Trust Security with Micro-Segmentation
Segmentation has been around for a long time there’s nothing new. There’s nothing sexy in it, we been doing segmentation for years. However, it is done specifically for network optimization and network performance, and it’s neither for security nor for compliance. Micro-segmentation however is a concept that is designed and purpose-built for security. In this blog, we will discuss zero-trust security with micro-segmentation and few considerations
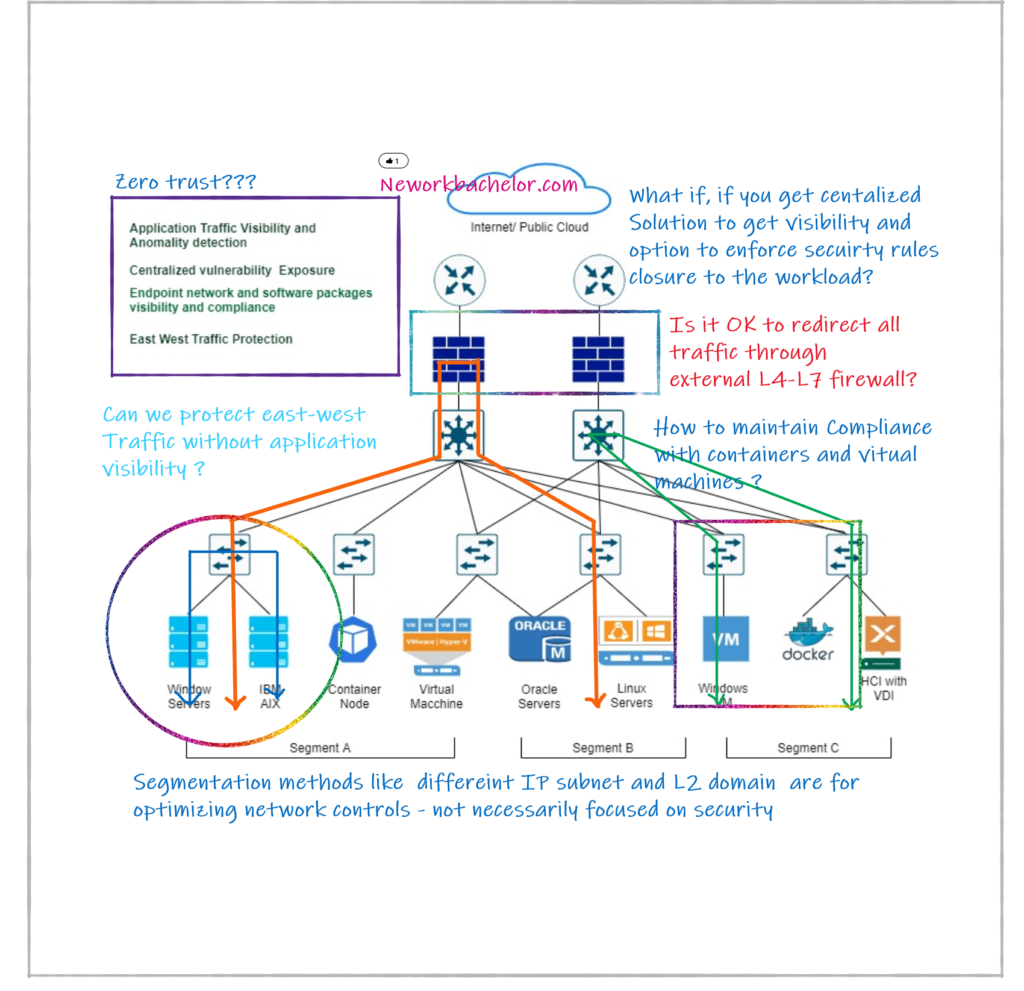
Why a New Approach to Zero-Trust Required?
The modern application and business models demand anywhere access and processing. With the cloud proliferation of mobile IoT and OT, the traditional security controls are no longer sustainable from economic or from the business processing perceptive. And moreover, currently with application workloads spans across on-premises, to edge to the cloud, it is tough to say where the perimeter begins and ends. This really complicates the security and control and enabling compliance on it
Now let’s discuss using the traditional model like physical or virtual firewalls. Yes, you may want to go buy firewalls and use these solutions to do your micro-segmentation. However, think about the complexity it brings when you do security policies and postures, as well as meet compliance requirements. Think about the sheer number of access control lists and firewall rule sets you’re going to have to build in places. And also maintaining that and who’s going to age those things off. By the time you know, they become points of vulnerability and points of escalating costs
Changing Compliance Requirements
Another challenge is, adapting compliance requirements changes in your network. How does your network change, and at what will be the cost of implementing the required changes on the infrastructure?. Apparently it is a huge burden on the folks that are maintaining the network and the security posture of an organization. Let’s take look at mergers and acquisitions from corporations like General Electric perspective. They’re working in the health field, financial sector, power sector, and transportation sector, etc, and they’re also working in the ICS industrial control and the ICS IoT world. Think about just that one use case how many standards that they have to comply with for their infrastructure, that’s before we even, talk about security.
So how do you build a network that can enable you to compliant irrespective of the changes put in place?. And keep in mind, if you’re doing it with hardware, you’re going to run out of money very fast, and just in terms of sheer complexity. it’s just it’s an untenable situation is the bottom line.
Real Worl Scenario Analysis
In my experience, a lot of times an organization building security infrastructure is to meet compliance standards, not for security. Security was almost seen as an afterthought. In fact, a lot of times, when you read the after-action reports on a lot of these hacks and breaches. The interesting questions basically pop-ups are, not how much data did we lose or money did we lose. The question was, were we compliant, at the time of the breach because if we were compliant nobody goes to jail !!
How Micros-segmentation is Helping?
By doing micro-segmentation we are actually doing two things- increasing the level of compliance and security.
Micro-segmentation with zero trust policy reduce the audit scope and attack surface that is presented to my compliance requirements. And don’t forget, the very reason that we have compliance standards in the first place is to protect data. With micro-segmentation, we are talking about protecting each of the east-west traffic flowing across your workloads within or between the on-prem datacenters and cloud. A simple analogy could be, you know, when you rob a bank, you open the door. And there’s all your money, right. That’s the easy way. That’s segmentation. What we’re talking about here with micro-segmentation is opening that vault door, and inside the vault door is yet more vault doors. And then when I get inside those vault doors, there are probably smaller compartments in there
In short, with micro-segmentation, it becomes a very interesting proposition in terms of compliance and zero-trust for your application as well as presenting a very tough problem set for an attacker.
Summary & Next Steps
Importantly, there are two things to consider, 1) protect customer data from insider and outsider threats 2) maintain compliance. If you think about compliance is a static snapshot, but yet organizations will spend a lot of money, just trying to maintain and validate that one snapshot which typically happens once a year. My question to them would be what if it creates a detriment to the overall security posture of the organization ! so this is the time to look at it from compliance & also specifically from a security perspective. And the good news is, for both of these cases modern solutions on micro-segmentation really helps
For more information and read, I would encourage you to go through the micro-segmentation solutions such as Cisco Tetration and VMware NSX and for compliance requirement details, please visit PCI security standards
Happy Learning

this article was helpful in understanding the micro-segmentation requirements. Thanks, Marakkottahil for simplifying it.
Zero-Trust is clearly the present and future of Security with micro-segmentation being a key tenet of it. Good one MM.