How Traffic Managed with NSX Microsegmentation
Microsegmentation is a method of creating different landing zone to separate the workloads. This method brings the security by isolating the workloads and secure them individually. In traditional segmentation model we have always aligned with security policies with the environment rather than with applications.
With the traditional segmentation process the shared services can transverse tier boundaries without being checked, which brings major threat. Usually the attackers target low-priority systems often and gives them the path to attack other systems in the environment. You will see in this blog how traffic is managed and protected with NSX microsegmentation
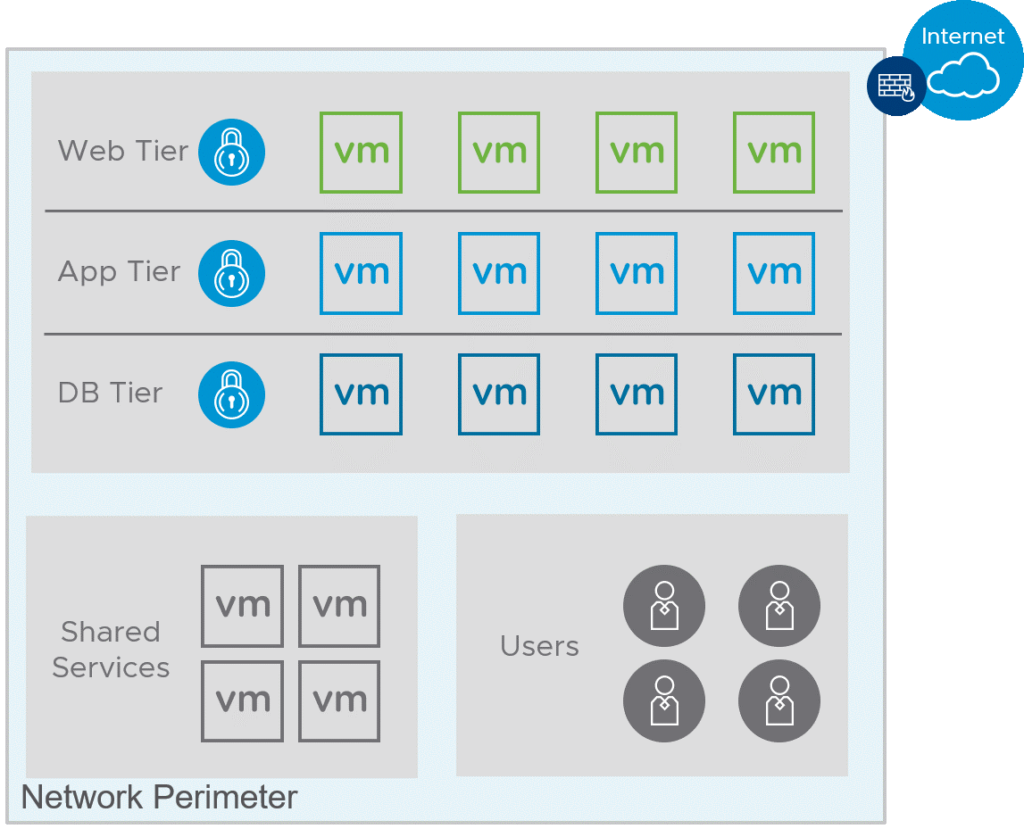
Microsegmentations vs. VLAN’s, Firewalls and ACLs
Well microsegmentation isn’t new in most of the environment it has been implemented either with the help of separating the workloads based on L3 subnet, VLAN. Furthermore, these entity is being used to write the respective rules on firewall or as an access-list. Based on application type the polices may vary. In short, using VLAN you can achieve segmentation but micro-segmentation helps you to do a granular segmentation, Ex: isolating endpoints
How traffic is managed in Traditional Data Center
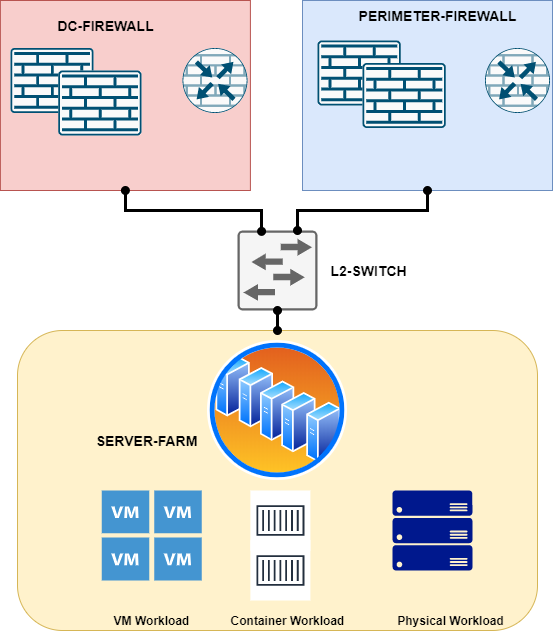
Indeed, in any traditional infra usually you could find firewalls protecting External and Internal traffic. Moreover Internal firewall are pretend to segment the East-West traffic.
Additionally, modern workloads are in the form of virtual machine and containers which sits on the any of the virtualised solutions. But to accomplish segmentation of traffic we need to send it right from workloads to firewall. This kind of hair-pinning will cause more complex traffic management and gives hard time to troubleshoot.
How Traffic Managed with NSX Microsegmentation
VMware NSX uses distributed firewall (DFW), with the help of DFW it logically divides a data center into distinct security segments down to the individual workload/VM level. This gives power to distinct controls and security services based on applications. Therefore, specific application will have their respective rules which can be managed and operated centrally and applies the rule to each VM’s vnic level.
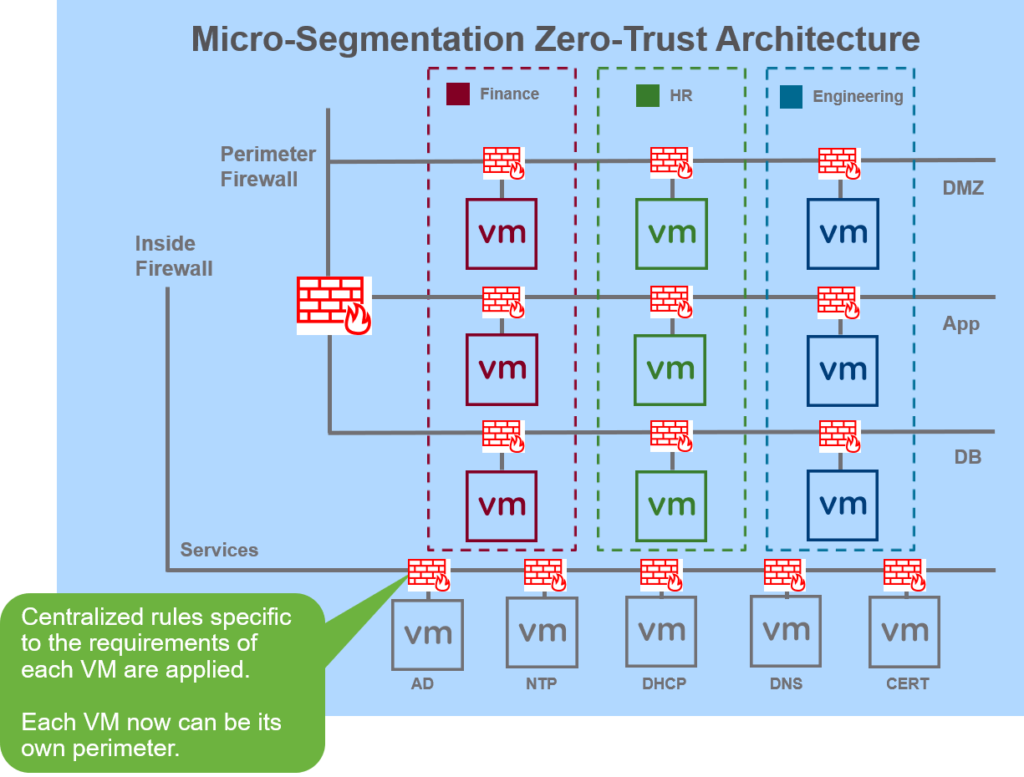
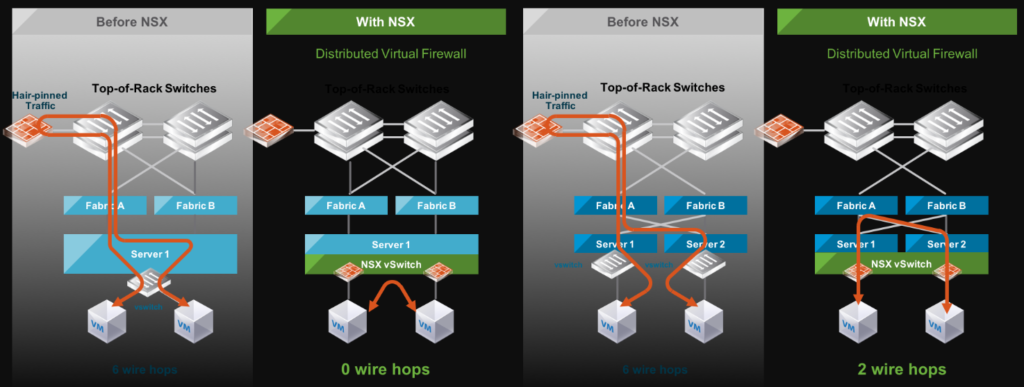
Regarding traffic pinning we will see that it won’t require to send the traffic to physical firewall, therefore, reducing traffic reaching the upstream network or firewall. Furthermore, for detailed use case and benefits you can refer VMware published whitepaper on microsegmention
And for key features on NSX 3.0.0 version please refer this blog
Summary
Finally, this article described the microsegmentation and how it is implemented in VMware NSX. Part 2 of this blog series will be published and will explain the detailed configuration steps.


Hi Abhishek,
Very lucid article about NSX micro-segmentation. I would like to add that in NSX also it is possible for shared services/processes to communicate with VMs across isolated VM environments. In today’s enterprise network, it cannot be completely done away with it. But surely, the choice of such services always remain with the enterprise.
Thanks,
Susmita