VMware Design Bootcamp-4: NSX-T and AVI Load-balancer
Currently, most of the business runs on applications. And apparently, faster infrastructure provisioning is required to support the on-demand nature of modern applications. Secondly, integrating heterogeneous infrastructure solutions to support application hosting is another common challenge faced by the customers. In reality, most of the customers are having top-notch solutions from different vendors, which may provide best-in-class forwarding performance. But managing these heterogenous systems are a huge threat to the simplicity and agility expected out of the infrastructure
VMware Approach to Networking and Security: Introducing NSX-T and AVI
To start with, VMware NSX-T and AVI load-balancer functions are based on SDN principles. The SDN preaches a controller-based solution to configure, deploy, and manage the end-to-end solutions and data plane to process the traffic. With NSX-T, the “NSX-T manager” manages and controls the end-to-end network and security stack, and hypervisor system such as ESXi and KVM does the data processing. With AVI “AVI controller” centralizes the management and controlling of the ADC functions such as LB, GSLB, and WAF, etc and the AVI services-engine does the data plane function. In a nutshell, the network & security block in a software-defined infrastructure play a key role in providing compliance, cost efficiency, and agility, etc. VMware made it easy to attain these business objectives using its virtualization offerings.
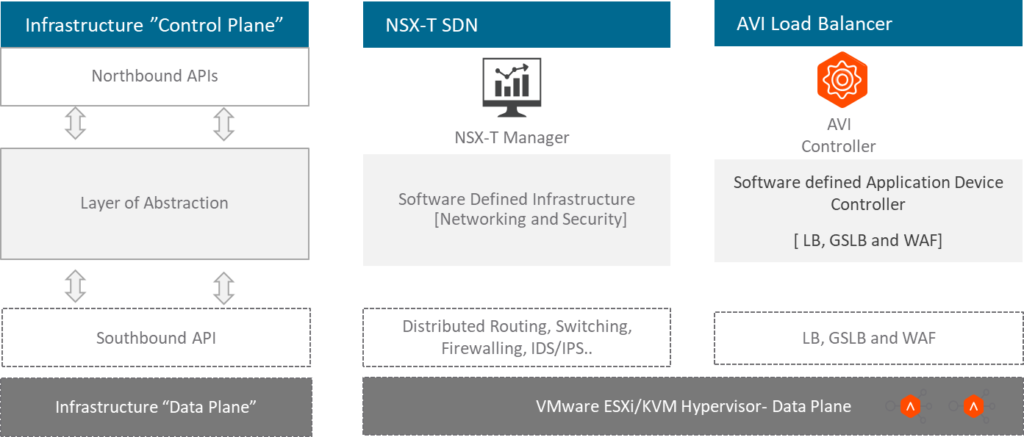
Integration- An Architectural perspective: NSX-T and AVI
Now let’s look at how NSX-T and AVI load-balancer solutions from an architect’s point of view. And see how this fits into an enterprise-grade network topology. Usually, the enterprise can have a single site or multiple sites, and for each site, you can have multiple segments such as production, development, and DMZ, etc. To understand the segmentation and its needs, for example, for the production segment, all the workloads part of the production will connect to its dedicated NSX-T1 logical router for the gateway services. And T1 router can also use it for connecting to the specific L4-L7 services. To connect to the outside NSX-T domain such as the physical firewall, physical routers, the NSX-T T0 logical router will be used. The same semantic applies to the development and DMZ segments etc.
The DMZ will host the published applications. And for the same reason, it should be more secure. The AVI load-balancer with web application firewalling and GSLB meet some of the prominent use cases for DMZ.
Using GSLB you can make sure applications are load shared across the DC’. And with the help of the NSX-T federation the required network and security services for the application can be stretched across multiple sites.
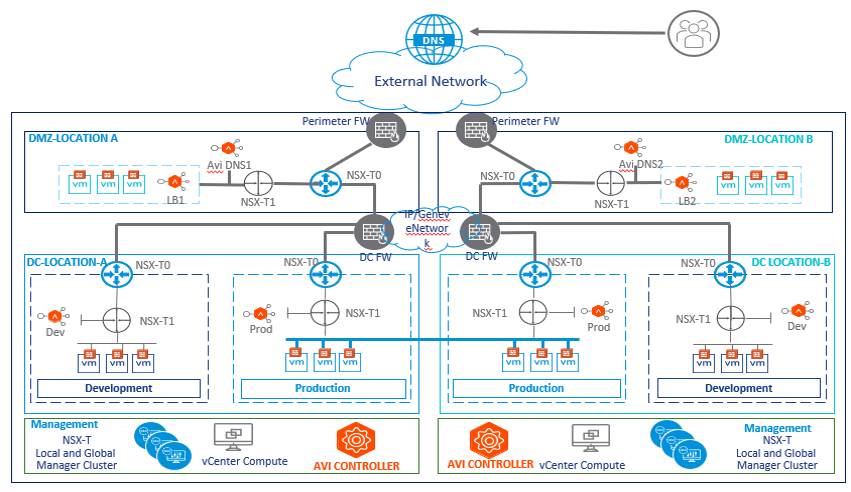
Use Case 1: Integrated Networking & L4 -L7 Services
To integrate AVI load-balancer with NSX-T, you need to provide an NSX-T credential on the AVI controller. Then, from the AVI you will be able to see all the network policies provisioned by the NSX-T
The NSX-T and AVI together can take care of the end-to-end network, security, and ADC use cases for a DC infrastructure. To understand the integration use case, the NSX-T manager centrally manages the routing and security and by integrating with AVI, it also allows to address load-balancing, GSLB, and IPAM, etc.
Use Case 2: Scalable Application Delivery Infrastructure
Currently, most of the company runs their business on the internet. Depends on the nature of the business you may see there is a huge spike during some festive seasons like Christmas and Eid. The infrastructure should be able to scale out and scale in according to the demand. With AVI you can easily set a threshold, such as if the resource utilization reaches a certain level, let’s say 70 or 80% it can scale out and automatically provision additional service engine to support the extra traffic load.
Use Case 3: End-to-End Monitoring & Visibility
The performance of the application is critical for business success. Troubleshooting and identifying application issues are challenging. The issue could be anywhere between the client connecting infrastructure and to load-balancer. And some cases are due to the real-servers or could happen due to the application stack itself. With AVI you can get granular details about each of the hops and its RTT (Round trip time) to derive insight on the issue.
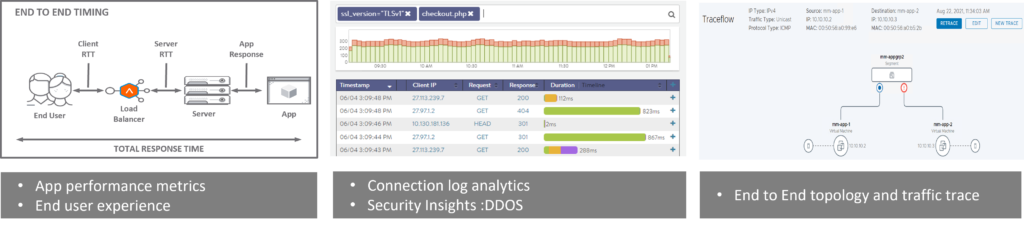
Now, few notes on the analytics provided by AVI. The connection log analytics on AVI. can help with the end-to-end client details. such as what is the user agent/browser it uses for sending the requests. Maybe it uses firefox, chrome, and internet explorer, etc. And also it can capture details about client OS, device, location of the client, end-end timing, user ID, etc. For example, it captures operating system details such as android, IOS, and Windows, etc – these data could help in better understanding client profiles and further help in isolating the issues
Finally, concerning the infrastructure, the NSX-T allows end-to-end troubleshooting. From the source to the destination. It can give hope by hop details and also can tell you whether the traffic is getting affected due to firewalling issue or due to some other routing issues
Conclusion
If you have, your network and security and ADC solution integrated end-to-end it could simplify the infrastructure management and provisioning to a large extend. It is important to note that NSX-T and AVI solution works very well with VMware infrastructure but could also work with bare-metal systems with a proper plan and execution in place.
For more related blogs on the topic – please refer to the section “Datacenter networking & security“ happy learning